In the IT systems landscape, using usernames and passwords for authenticating systems often causes lots of headaches such as password storage and retrieval, hardcoded or deployed passwords, password change frequency and impacts of password changes.
When it comes to SFTP (SSH File Transfer Protocol), a better option is using key pair based SFTP. This blog helps to outline the steps required when you want to configure Oracle Service Bus (OSB) 11g to utilise key pair based authentication for SFTP (SSH File Transfer Protocol). For public key authentication, the SFTP server authenticates the connection with the public key of the OSB service.
Assumptions
- This blog will focus on “inbound” SFTP connections using OSB (i.e. proxy services which poll a given directory via SFTP and downloads the file from the SFTP server) however, the same configuration should allow outbound SFTP connections as well. The ALSB service (proxy and business) always acts as the SFTP client and connects to the SFTP server.
- The ‘oracle’ user is used to start the OSB server
- The remote host to which the OSB will connect via SFTP is ‘soabpm-vm’
- The ‘osbsftpinsystemdev’ user is used to perform the SFTP retrieval from ‘soabpm-vm’
- The ‘osbsftpinsystemdev’ user already exists on ‘soabpm-vm’
- The java keytool utility is available for use by the oracle user
- The openssl utility is available for use by the oracle user
SSH Key Configuration
Generate SSH key pair for oracle user
In order to allow key based authentication, we need to generate SSH keys for the oracle user using the below command:
ssh-keygen -t rsa -C “oracle@soabpm-vm”
After providing responses to the few questions, this will create two files within the ~/.ssh directory, one containing the private key and one containing the public key (.pub):
id_rsa and id_rsa.pub
Allow key based SSH authentication for the oracle user on SFTP Server
Now that we have generated the SSH key for the oracle user, we need to allow the oracle user to login to soabpm-vm as the osbsftpinsystemdev user without having to provide a password by performing the following:
1) Login to soabpm-vm as the osbsftpinsystemdev user
2) Create the ~/.ssh directory with the required permissions using the following:
mkdir ~/.ssh
chmod 700 ~/.ssh
3) Create the authorized_keys file with the required permissions as follows:
touch ~/.ssh/authorized_keys
chmod 600 ~/.ssh/authorized_keys
4) Copy the content of the oracle user’s ~/.ssh/id_rsa.pub (public key) file into the osbsftpinsystemdev user’s ~/.ssh/authorized_keys file and save the file
5) As the oracle user, verify that you are able to connect to soabpm-vm as the osbsftpinsystemdev user without providing a password from the osb managed servers:
ssh osbsftpinsystemdev@soabpm-vm
- If you receive a message stating that the authenticity of the host cannot be established, type ‘yes’ to continue and the RSA key fingerprint will be added to the oracle user’s ~/.ssh/known_hosts file. Note that this should only happen the first time you connect (assuming that you always use the same name to refer to the remote host)
- If you are prompted for a password, ensure:
(i) The permissions on the osbsftpinsystemdev user’s ~/.ssh directory and ~/.ssh/authorized_keys file are correct
(ii) The content of the osbsftpinsystemdev user’s ~/.ssh/authorized_keys file exactly matches the content of the oracle user’s ~/.ssh/id_rsa.pub file
(iii) Note that if you regenerate the oracle user’s ssh keys, you will need to remove the existing public key from the authorized_keys file and insert the new public key
Import SSH Keys into OSB Keystore
Now that the oracle user is able to utilise SSH keys to establish a connection to soabpm-vm as osbsftpinsystemdev, we will add the same keys to the keystore used by the OSB server to enable OSB to utilise them as well.
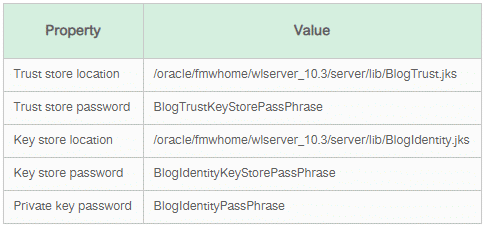
1) Determine the location of the identity keystore in use by the OSB server. This can be obtained through the Admin console by navigating to Environment > Servers > OSB server > Configuration > Keystores. In this blog, we are using the demo identity and demo trust keystores which have the following properties:
2) As the oracle user, run the following to remove the key with alias ‘oracleSshKey’ alias if it already exists:
keytool -delete -alias oracleSshKey -keystore
/oracle/fmwhome/wlserver_10.3/server/lib/
BlogIdentity.jks -storepass BlogIdentityKeyStorePassPhrase
3) Convert the oracle user’s ssh key to X509 PEM format:
openssl req -new -x509 -days 3650 -key ~/.ssh/id_rsa -out ~/.ssh/x509_certificate.pem
- This will prompt you for a number of fields, but you can safely accept the defaults
4) Convert the X509 PEM certificate into P12 format:
*openssl pkcs12 -export -in ~/.ssh/x509_certificate.pem -inkey ~/.ssh/id_rsa -out ~/.ssh/keystore.p12 -password:BlogIdentityPassPhrase*
- Note that a password must be provided and in the above, we are providing it on the command line
5) Import the P12 keystore into the identity keystore using alias ‘oracleSshKey’:
keytool -importkeystore -deststorepass BlogIdentityKeyStorePassPhrase -destkeypass BlogIdentityPassPhrase -destkeystore
/oracle/fmwhome/wlserver_10.3/server/lib/BlogIdentity.jks -srckeystore ~/.ssh/keystore.p12 -srcstoretype PKCS12 -alias 1 -destalias oracleSshKey -srcstorepass BlogIdentityPassPhrase
- Note that the password for the P12 keystore must be provided and in the above, we are providing it on the command line
6) List the contents of the identity keystore and verify that the oracleSshKey alias is listed as a ‘PrivateKeyEntry’:
keytool -list -keystore /oracle/fmwhome/wlserver_10.3/server/lib/BlogIdentity.jks -storepass BlogIdentityKeyStorePassPhrase
Configure Credential Mapping Provider
Navigate to the Admin Console and perform the following to create and configure a credential mapping provider:
1) Within the ‘Change Center’, click ‘Lock & Edit’
2) Navigate to Security Realms > myrealm > Providers > Credential Mapping
3) Click ‘New’
4) Provide the following details:
- Name: oracleSshKey
- Type: PKICredentialMapper
5) Click ‘OK’
6) Click the newly created credential mapping
7) Select Configuration > Provider Specific and provide the following details:
- Keystore Provider: (blank)
- Keystore Type: JKS
- Keystore File Name: /oracle/fmwhome/wlserver_10.3/server/lib/BlogIdentity.jks
- Keystore Pass Phrase and Confirm Keystore Pass Phrase: BlogIdentityKeyStorePassPhrase
8) Click ‘Save’
9) Within the ‘Change Center’, click ‘Activate Changes’
10) Restart the server
Configure Credential Mapping
Navigate to the Admin Console and perform the following to create and configure a credential mapping:
1) Navigate to Security Realms > myrealm > Credential Mappings > PKI
2) Click ‘New’
3) Provide the following details:
- Protocol: sftp
- Remote Host: soabpm-vm
- Remote Port: 22
- Path: (blank)
- Method: (blank)
4) Click ‘Next’
5) Provide the following details:
- Credential Type: Key Pair
- Principal Name: osbsftpinsystemdev
- Principal Type: User
- Credential Action: (blank)
- Keystore Alias: oracleSshKey
- Password and Confirm Password: BlogIdentityPassPhrase
6) Click ‘Finish’
7) Ensure that the message ‘The security credential has been successfully created’ is displayed
Create Service Key Provider
Navigate to the OSB Console and perform the following to create and configure a service key provider:
1) Within the ‘Change Center’, click ‘Create’
2) Click ‘Project Explorer’ and navigate to the desired directory
3) In the ‘Create Resource’ drop down list, select ‘Service Key Provider’
4) Provide Service Key Provider Name as ‘soabpm-vm’
5) Click in the ‘Description’ text box to enable the ‘Browse’ buttons
6) Click ‘Browse’ for the ‘SSL Client Authentication Key’
7) In the pop-up window which appears:
- Select ‘oracleSshKey’
- Provide the private key password of selected key (in this case, BlogIdentityPassPhrase) in the textbox near the top of the window
- Click ‘Submit’ to close the pop-up window
8) Click ‘Save’
9) Within the ‘Change Center’, click ‘Activate’, provide a description and click ‘Submit’
Note that while it is easier to create the service key provider within the OSB Console, once created, it can be exported and stored within source control. Using this approach allows the service key provider to be referenced by the OSB services within eclipse included as part of the OSB deployment. The following section (‘Update OSB Inbound SFTP Proxy Services’) assumes that this has been done.
Update OSB Inbound SFTP Proxy Services
The final step is to update the OSB proxy service to utilise the service key provider as follows:
1) Ensure that the service key provider has been exported from the OSB Console as outlined in the previous section (‘Create Service Key Provider’)
2) In Eclipse, open the inbound SFTP proxy service
3) Select the ‘SFTP Transport’ tab and update the following fields:
- User Authentication: Public Key
- Service Key Provider: Click ‘Browse’ and select the required service key provider
- Username: osbsftpinsystemdev
4) Deploy OSB to the server and verify that the OSB proxy is able to retrieve files without issues
5) If you encounter problems:
- The OSB domain log file provides reasonable logging around the SFTP transport and it should highlight if the problem is with:
(i) Authentication – ensure the keys have been configured correctly
(ii) Permissions – check that the osbsftpinsystemdev user is able to navigate to the desired polling directory and has access to the required files
While the above may seem a little tedious, it is possible to automate everything outlined in this blog.