“Authentication is the process of verifying that an individual, entity or website is whom it claims to be” – OWASP.org
Multi-Factor Authentication (MFA) – and Two-Factor Authentication (2FA) – means that a user is required to show more than one type of evidence in order to authenticate on a system. It is important to highlight that it’s not enough to have two different instances of the same factor to achieve MFA.
The Four ‘Factors’ of Authentication
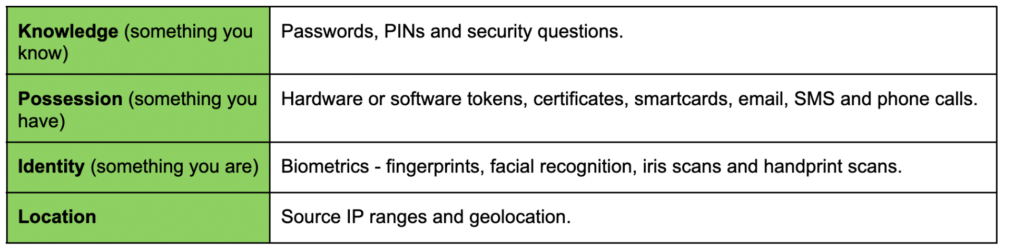
The authentication process generally begins by entering credentials such as a username and password. A weak password implies that the entity is more exposed to identity theft. Attacks like phishing, keystroke logging or password spray are some of the many methods attackers use to break passwords. Thus, the first line of defence on any system must then be to request strong passwords for their users.
Best practices for stronger passwords are:
- Require long passwords or passphrases (hard to guess, easy to remember)
- Avoid previous passwords reuse
- Use of combination of upper/lower case
- Use of numbers and special characters
The system should also have in place a back-off policy, login attempt rate limit, and generic login error messages.
With security threats becoming more prevalent, MFA is the best defence against the majority of password-related attacks. Additional factors of authentication make it much harder (if not impossible) for an unauthorised user to gain access to the system. Moreover, MFA should not only be used as part of the login process but also when the user performs sensitive actions such as changing passwords or financial institution details.
Which ‘Factor’ Type Best Suits my System?
Each authentication factor type has pros and cons, and so choosing what is right for you will depend on your individual business use case. The Open Web Application Security Project provides an informative ‘cheat-sheet’ worth reading, which we have linked to the bottom of this blog if you want to decide which factors best suit you.
The Process of Implementing MFA
While implementing MFA on your own can be challenging, doing so will give you complete control over the process. You’ll need to decide which factors to use and when to require MFA, along with other important security-related decisions such as back-off policies and rate limits. Although this creates more security areas to cover, you will probably have a more flexible solution that can adapt to the system needs.
If you would prefer to use a solution there are a plethora of options, provided by companies like Auth0, Okta, Twingate, Ping and CyberArk, to name a few. Each one of them has different factors and options available. Your decision should be based on the system requirements, budget and ability and technical knowledge to administrate the solution. Having MFA in place will likely demand an upskill for your technical team.
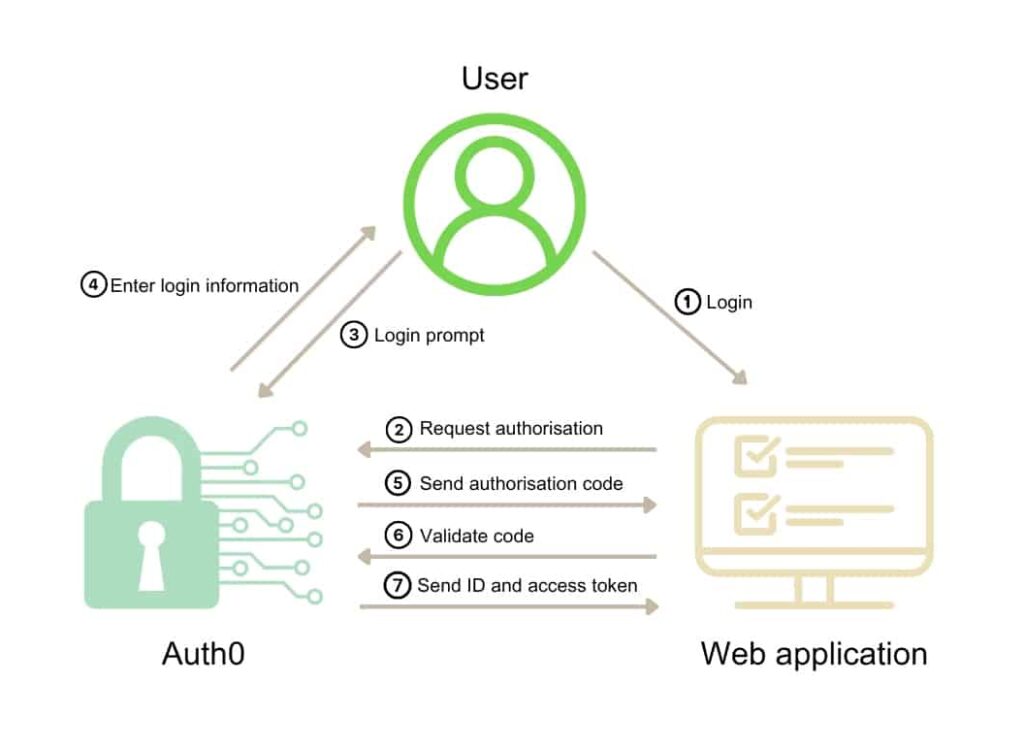
We have implemented solutions to improve the authentication process and thus improving system security. The first step in every solution generally involves creating stronger password rules, and enforcing authentication not just for login purposes but for administrative tasks, when needed. The solution provided by Auth0 offers all that in a way that is easy to integrate in existing applications. It also provides OAuth integrations using standard services like Google or Facebook. From a technical perspective, the authentication process is orchestrated by the Auth0 API, with minor modifications to the existing login process.
The authentication process begins with the user accessing the login page of an application (1). The application then forwards the request to the Auth0 authorization server using the SDK provided (2). Auth0 redirects to the custom login page for the tenancy (3). The user enters the login information based on what is configured. It is usually the credentials but it can also involve MFA steps orchestrated by Auth0 (4). Once the process finishes, Auth0 will send the authorisation code to the web application (5), and the application will validate the code against auth0 using the client id and secret which are unique for each tenancy (6). Finally, Auth0 will return a token, access token and, optionally, a refresh token (7). From there, the application can use that temporal token to further interact with the user.
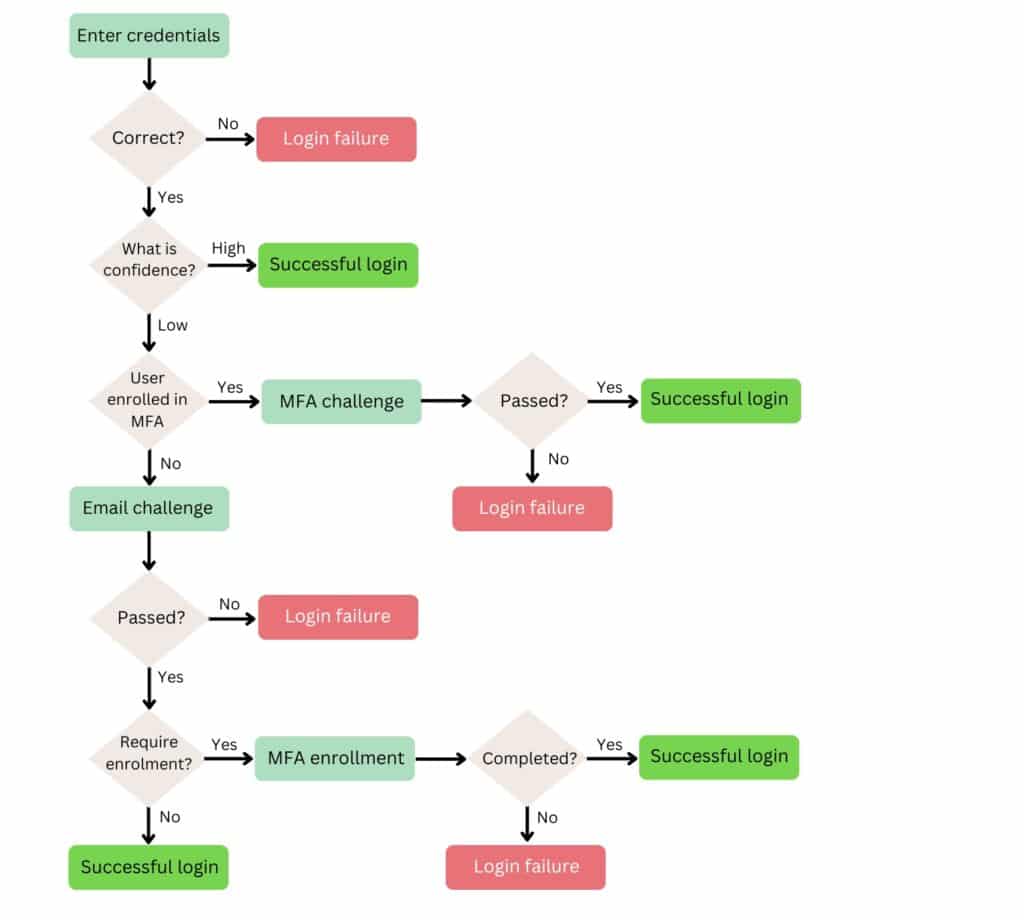
The next step is to add MFA on top of the existing process. The Possession factor is the preferred one, and Email and TOTP (Time-based One-Time Password) are the most popular options, given that SMS messages are less secure (1, 2).
We also used the location factor to provide adaptive MFA, meaning that the user would require MFA in case the IP range is outside a certain IP range. That is to ensure that the authentication process occurs in a specific place (e.g. the company headquarters), or MFA is required to ensure the authentication attempt is not an attack.
Here is a typical interaction between the user and the system when MFA is present:
Example Use Case
We had a customer with a unique requirement of having hundreds of generic users to log in to their system for a specific duration of time. To address this requirement, we implemented Passwordless authentication, which involved users entering their email address in the login page and receiving a TOTP code via email. The generic email accounts were managed by the customer, making it their responsibility to ensure security by managing and controlling access to these email accounts. The Passwordless authentication approach not only met the customer’s needs, but also provided an additional layer of security by eliminating the need for users to remember and enter their passwords. However, it’s important to note that the security of this approach heavily relies on the customer’s commitment to managing and securing the generic email accounts. It’s critical for the customer to establish appropriate policies and procedures to protect the email accounts from potential threats.
Scalability
Scalability is one of the key advantages of adopting MFA in your business. A scalable MFA solution can be customised to meet the specific requirements of any company, regardless of its size or maturity level. This means that the MFA solution can grow together with your business, without requiring any significant modifications or disruptions to your existing processes.
Smaller businesses may find it more suitable to use text messages or mobile applications for their MFA solution as these options are relatively easy to implement and manage. However, as the company expands, it may become necessary to leverage more advanced hardware-based solutions such as smart cards or biometrics. Larger businesses can take advantage of cloud-based solutions that are scalable and cost-effective, allowing them to easily manage authentication needs for a growing number of users.
The chosen multi-factor authentication solution may differ between organisations, based on their unique complexities and level of maturity. By selecting an MFA solution that can adapt to your changing needs, you can ensure that your authentication process remains secure, efficient, and cost-effective over the long term.
References
Open Web Application Security Project Cheat Sheet
1 Shin, J. (2023) What to Do About the Vulnerability of SMS-Based Authentication https://www.tyntec.com/blog/what-do-about-vulnerability-sms-based-authentication
2 Authgear (2023) Is SMS OTP Reliable? Its Vulnerabilities and Alternatives https://www.authgear.com/post/sms-otp-vulnerabilities-and-alternatives

